TLS 1.2 needs strong encryption capabilities. TLS 1.2 defines certain cipher suites to be used to enforce strong encryption. A list of the TLS 1.2 cipher suites can be found at the OpenSSL site or in the RFC 5246 document.
What is a cipher suite?
A cipher suite is a named combination of cryptographic algorithms. The TLS protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks:
- Key exchange
- Bulk encryption
- Message authentication
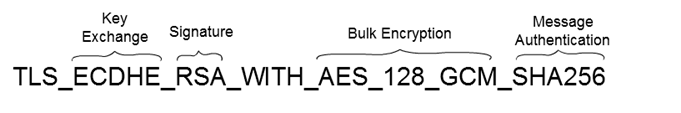
Key exchange algorithms protect information required to create shared keys. These algorithms are asymmetric (public key algorithms) and perform well for relatively small amounts of data.
Bulk encryption algorithms encrypt messages exchanged between clients and servers. These algorithms are symmetric and perform well for large amounts of data.
Message authentication algorithms generate message hashes and signatures that ensure the integrity of a message.
Limitations of standard installation of Java
Due to import regulations in some countries, the standard Oracle JRE provides a default cryptographic jurisdiction policy file that limits the strength of cryptographic algorithms. The Java website lists the maximum key sizes allowed by this version of the jurisdiction policy.
This means, Java’s default cryptographic functionalities have limitations related to the size of keys, e.g. Java by default supports only AES with a 128 Bit key. The restrictions are related to the US law and are supposed to prevent the application from using stronger ciphers.
OpenJDK seems to have no limitations of the key sizes.
Stronger encryption
If stronger algorithms are needed (for example for TLS1.2 using AES with 256-bit keys), the JCE Unlimited Strength Jurisdiction Policy Files must be downloaded and installed in the JDK/JRE.
The Java Cryptography Extension (JCE) is an officially released extension to the Java Platform and part of Java Cryptography Architecture.
JCA delivers the most basic cryptographic features. JCE provides various advanced cryptographic operation with longer keys resulting in stronger encryption.
Installing JCE
You can install the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files. Download the files and instructions for Java 7 or Java 8.
- Locate the
jre\lib\securitydirectory for the Java instance. - For example, this location might be:
C:\Program Files\Java\jre8\lib\security. - Remove the following
.jarfiles from this directory:local_policy.jarandUS_export_policy.jar. - Replace these two files with the
.jarfiles included in the JCE Unlimited Strength Jurisdiction Policy Files download.
There is no way to distribute the files with your program; they must be installed in the JRE directory.
How to avoid installing “Unlimited Strength” JCE policy files?
To the best of my knowledge, there is no reliable workaround to install the JCE policy files if you are using an Oracle JDK or JRE.
- Some websites mention a reflection based workaround to enable stronger encryption but this is reported to not work with TLS1.2 ciphers.
- Using another cryptography library such as Bouncy Castle won’t let you use 256-bit TLS cipher suites, because the standard TLS libraries call the JCE internally to determine any restrictions.
It might be possible to use OpenJDK without installing JCE if that’s an option for your application.
